Authors: Phillip Porras, Project SE-RAN – The Security-Enhanced Radio Access Network (5GSec.com), Accuknox Inc., Ohio State University, and SRI International
Introduction
Within the Nephio project and the broader Linux Foundation’s 5G initiative, we have the opportunity to introduce critical runtime security services into mobile network infrastructures, which can reshape the security and resilience of O-RAN compliant networks for decades to come. Developing a robust and operationally sustainable 5G network infrastructure should include an early and thoughtful examination of the services needed to validate and securely manage its operations. Our goal is to enhance the trustworthiness of 5G networks with respect to mobile device confidentiality and privacy, 5G communications integrity, survivability, accountability, resistance to attacks, including attempts at control-plane infiltration, as well as the live detection and identification of attacks against the mobile infrastructure and its users.
Our vision is to foster a community that creates modular O-RAN-compliant security components to enhance the deployment and runtime management of mobile network infrastructures. In particular, these solutions should extend the existing O-RAN consortium’s open software architecture to tackle at least two fundamental problems. The first problem is the extensive attack surface that arises from the migration of the mobile network control plane into a cloud-based operating environment. While the integration of the RAN Intelligent Controller (RIC) into a Kubernetes framework dramatically increases the scalability and extensibility of control logic, it also exposes the control plane to the breadth of adversarial tactics and open-source supply chain vulnerabilities that plague existing cloud ecosystems [58, 12]. The second problem is the existing lack of visibility into core 5G network operations: one cannot secure the mobile network if one cannot observe its operations with sufficient granularity. Our approach is to introduce the first security-focused, base-station-internal telemetry stream that will facilitate runtime security monitoring within the O-RAN compliant 5G Open-Source Software (OSS) ecosystem.
Figure 1 illustrates three of our initial O-RAN security modules and their integration points within O-RAN-compliant 5G networks. The MobiFlow Auditor represents a centralized unit (CU) E2 service model, producing a security audit trail that is streamed to the control plane via O-RAN’s open E2 interface. MobiFlow’s purpose is to drive in-depth exploit and anomaly detection algorithms that require a state-transition-level understanding of the (OSI) layer-3 (L3) communications between each base station, client device, and potential adversarial RF-emitting entities that may be in range of either the base station or its clients. 5G-Spector represents the first L3 runtime intrusion detection system for combatting the growing number of malicious RF protocol exploits. 5G-KubeArmor is our 5G-native runtime security enforcement system that restricts the behavior (such as process execution, file access, and networking operations) of xApps and the nRT-RIC operations at the system level. Its role is to enable 5G operators and control-layer DevOps teams to derive and enforce individual least-permissive policies across all control-plane applications. The bottom left panel of Figure 1 illustrates the familiar O-RAN 5G software-defined architecture. Each of these components leverage O-RAN’s open API and modular design to integrate with a minimum of disruption and porting required across the primary software sub-systems: the Centralized Unit (CU), Distributed Unit (DU), and the RIC. The bottom right panel in Figure 1 illustrates the insertion locations of the three SE-RAN security services within the O-RAN mobile network.
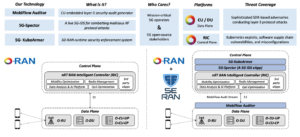
Figure 1: Technology summary of our three initial O-RAN compliant security services: MobiFlow Auditor, 5G-Spector, and 5G-KubeArmor. The top panel summarizes each technology, and the bottom panels illustrate the integration locations of each service in the O-RAN software-defined mobile network architecture.
O-RAN Security Challenges
While O-RAN’s architectural shift to an open-standards based software-defined paradigm represents a true advancement from prior mobile architectures, significant security challenges and deployment risks continue to emerge. These risks are substantial, even within private cloud ecosystems. Within the 5G OSS project community, our objective is to protect O-RAN networks from attacks that target the underlying mobile infrastructure. These threats can be broadly separated into two primary challenges: securing the control plane from infiltration and enabling efficient runtime security analysis of the data plane.
5G CONTROL PLANE SECURITY:
The 5G Open-RAN reference architecture separates the network control layer from the data and radio planes, and migrates the control layer into a virtualized cloud ecosystem. Here, the previously vendor-specific control and management functions are now separated and modularized as applications that are managed by a platform called the RAN Intelligent Controller, or RIC. The RIC is designed to run the control and management applications that govern 5G cell operations. These applications are highly business critical, and can even be public-safety critical.
The 5G SD-RAN control plane and runtime environment are, by design, now dependent on today’s open-source software supply chain. The movement toward K8s DevOps deployments exposes the 5G control plane to the inherent risks from open-source supply chain threats, malicious pre-infected libraries and images, zero-day vulnerabilities, Kubernetes malware, and increasingly sophisticated cloud-focused hacking groups. These risks are substantial, even in private cloud ecosystems.
The following are examples of threats arising within the Kubernetes-based ecosystems that have become inherited attack surfaces within 5G control plane deployments:=
- Substantial concerns exist regarding the trustworthiness of community application image libraries. For example, half of the virtual application images examined in one study were found to contain at least one critical vulnerability [23].
- One study, [62], found that even small releases of pre-infected virtual application images can be propagated across millions of operational container instances.
- Several studies [37, 58, 42, 53] have observed overwhelming increases to the number of nation-state and cyber-criminal exploits and vulnerabilities that are implanted into the software supply chain on which Kubernetes DevOps teams rely.
- There has been an emergence of sophisticated cloud-focused botnets, malware, and worms designed to infiltrate public and private Kubernetes instances [36, 21, 17, 29, 20, 69].
- Sophisticated Kubernetes-focused hacking teams have emerged that specialize in pod and container infiltration around the world [28, 67, 50].
- Vulnerabilities have been continually discovered throughout the open-source software tools and services that are used to manage and administer cloud workloads, including with Kubernetes itself [40, 63, 70, 55, 43, 25, 68].
The paradigm shift that O-RAN is pursuing (to migrate the 5G control plane to a virtual DevOps framework) is fraught with new and inherent attack surfaces that are necessary to address in order to create trustworthy 5G networks, and are of primary concern to 5G operations in mission-critical or safety-critical environments. The control plane is perhaps the most mission-critical component within a 5G network and requires extensive attention to its security and resilience.
5G DATA PLANE SECURITY:
Over the past decade, researchers in the security community have identified a wide range of exploits launched from low-cost and highly portable software-defined radios (SDRs) [2, 54]. These attacks can disrupt and compromise targets ranging from commercial user smartphones and base stations to mission-critical 5G infrastructures and equipment (e.g., drones, automobiles, and surveillance cameras), imposing various impacts such as serious privacy violations [32, 60, 13], confidentiality and integrity attacks [48, 73, 41, 27], denials of service [39, 31, 33, 18, 35, 56, 64], identity spoofing [61, 44, 15, 14], and device geo-tracking [41, 27, 22, 24]. Although these exploits were discovered in LTE networks, most of them still apply to the 5G protocol, which enables an adversary within signal range of a 5G network to potentially compromise its base stations or surgically attack individual devices. Even more concerning, these attacks are accessible to adversaries who use low-cost SDRs [2, 54] and open-sourced cellular software stacks [30, 9].
One major attack surface within the cellular data plane is the 5G L3 protocols that enable devices to establish sessions and authenticate with the base station. Mobile network adversaries can exploit these protocols to compromise the availability, confidentiality, and integrity of UEs and RANs, by manipulating, transmitting, and eavesdropping on unprotected cellular protocol messages [38]. This attack surface emerges due to the unprotected (i.e., not signed or encrypted) L3 protocol messages [34] such as those of the Non-Access Stratum (NAS) [10] and Radio Resource Control (RRC) [11] protocols, which are designed to handle the session establishment between the UE and the cellular network. Most of the aforementioned attacks fall into this category and can be conducted to trigger Denial-of-Service (DoS), geo-tracking, and service downgrade [33, 41, 59, 39, 73, 44, 18, 35, 56, 41] targeting either a UE or the RAN. Unfortunately, while protocol-level defenses have been proposed [12, 34, 65, 71], these vulnerabilities are hard to fix in contemporary cellular network infrastructures due to many concerns and constraints in terms of performance, compatibility, and usability. The following are three dominant adversary models that could possibly take advantage of these exploits, and that mission-critical 5G networks must address:
- Adversarial UE: With a commercial-of-the-shelf (COTS) SDR running open-source cellular software [30, 9] and a valid subscriber network identity (e.g., SIM), one can set up an adversarial UE. Further, attackers can modify the cellular protocol stack to perform availability attacks to compromise other victim UEs and the RANs. For instance, BTS resource depletion can be launched by continuously creating massive fabricated RRC connection requests to DoS a target base station [39, 33]. An adversary may also DoS a legitimate UE by replaying its identity (e.g., its TMSI) in an RRC connection request [39].
- MiTM Attacker: A man-in-the-middle (MiTM) adversary impersonates a legitimate base station that connects with the victim UE, and impersonates the UE to the real base stations, which thus requires two SDRs. A MiTM attacker can then replay or manipulate the session, by exploiting messages that are not encrypted or digitally signed [59, 61].
- MiTM Signal Injector: Most recently, it has been shown that MiTM adversaries can use an SDR to inject malicious signals to overshadow the downlink and uplink traffic while maintaining a high level of stealthiness (e.g., using slightly higher signal strengths such as 3dB more) [73]. As a result, this signal injection (or overshadowing) attack can be further exploited to launch privacy and availability attacks, such as a DoS attack [27] and an IMSI extraction exploit on UEs [41].
Unfortunately, existing defenses against these cellular exploits are mainly deployed on the UE side [26, 16]. The few proposed network-side defenses can only detect the existence of fake base stations [45, 52, 51]. In general, these defenses fall short, with a limited view (e.g., UE-centric defenses cannot detect RAN-targeted attacks) or poor extensibility (e.g., network-based solutions with static defense mechanisms). If one must rely on the security and integrity of a 5G network, then the runtime analysis of its operation must begin the moment that communications between device and base stations begin.
Securing the O-RAN Control Plane
As public cloud 5G networks are transforming the industry from closed proprietary control functions to virtualized private cloud deployments, the opportunities to rethink our notions of mobile network security posture management are also transforming. The O-RAN design separates the mobile network control and management functions into modular applications that are managed by a platform called the RAN Intelligent Controller, or RIC. Within any 5G network architecture, the RIC represents perhaps the most mission-critical system within the architecture. Within the Nephio project, and under the LFN 5G Super Blueprint activities [66], the Open-RAN RIC is hosted within a Kubernetes framework, and its control functions are containerized and deployed as extensible virtualized workloads (or xApps). While fostering improvements in scalability and extensibility, as well as providing greater flexibility in integrating novel mobile control logic, this migration of the 5G control plane into a Kubernetes-hosted ecosystem also introduces substantial security challenges. Thus, a key early driver for the community is to deliver a critical 5G-native (i.e., control plane aware) runtime security enforcement system that automates least-permissive security policy generation and enforcement, per xApp and the RIC.
The 5G control plane is perhaps the most mission-critical element of any 5G infrastructure, and likely to be among the highest-priority targets of sophisticated adversaries seeking to infiltrate or disrupt a 5G network. We need technologies that can lock down the control plane, automate the creation and enforcement of fine-grained least-permissive policies across every O-RAN RIC process, and thereby securing the control plane from the breadth of Kubernetes adversarial tactics, techniques, and practices.
As a reference implementation to address the control plane security challenge, we are developing a customized integration of our open-source project, KubeArmor, as a runtime security policy enforcement engine for managing the 5G control plane. KubeArmor is a Cloud Native Computing Foundation (CNCF) open-source security project that currently exceeds more than 400K downloads. It is an LSM and eBPF 3 runtime protection service developed for Kubernetes workload management, and for enterprise and edge IoT applications.
Our intent is to deliver an OSS release of 5G-KubeArmor within the Nephio and LFN community, to demonstrate an approach to addressing the critical need to lock down and monitor the security posture of the RIC and its xApps. 5G-KubeArmor will enable xApps to operate with least-permissive process-level constraints, authenticated and non-repudiable identities, data flow privacy, and RIC-wide runtime monitoring and policy enforcement to ensure compliance with an applicable set of 5G-specific security standards.
Using 5G-KubeArmor, we will explore 5G xApp workload monitoring solutions that spans the entire control plane and its programmatic interfaces. We will demonstrate the ability to derive and enforce least-permissive policy sets per xApp and for the RIC subsystems. Each permission model is based on an abstraction of key security-relevant system-call and argument activities involving file system interactions, process management, network activity, and administrative and shell functions. The policies are implemented in YAML, along with tools that enable the operator to inspect and augment these policies to capture exactly how each application should be constrained when deployed.
We intend to release a version of 5G-KubeArmor with the ability to conduct live 5G control plane policy monitoring and enforcement, stability and subversion detection, network security and identity management, and fine-grained data-flow protection. Part of our studies will also include the design of core compliance policies and cloud security principles that are necessary to field 5G networks within different operational domains. We plan to establish methods to synchronize security policy orchestration within the Nephio project’s intent-driven declarative management automation paradigm.
Enhancing O-RAN Visibility
To design in-depth monitoring services that can detect and mitigate threats from the 5G data plane, one must first address the visibility problem. Future O-RAN security services (e.g., intrusion detection, machine learning, and anomaly detection xApps) operating at the control plane should be able to monitor security-relevant activity from the CU/DU perspective, enabling them to identify the breadth of exploits that base stations are exposed to in hostile RF environments. We must design efficient security audit streams that capture sufficient information to drive analysis of the breadth of exploitations that can occur between devices and base-station protocols [39, 33, 41, 27]. We can confirm that the existing reference E2 Service Models (E2SMs) in the O-RAN specification [1], namely Key Performance Measurement (KPM) [7], RAN Control (RC) [4], and Network Interface (NI) [3], are insufficient for such sophisticated control-plane security services.
To address the visibility gap necessary to drive 5G threat monitoring services, we are designing a new CU/DU telemetry stream [71], and an O-RAN compliant security audit service that can modularly insert into O-RAN compliant CU/DU projects. Our telemetry stream, called MobiFlow, provides mobile devices accountability during the link and session establishment protocols (e.g., RRC [11] and NAS [10]), and enables the control plane to identify large-scale patterns of abuse against the base stations and mobile devices. MobiFlow is transmitted as stream records from the data-plane nodes (i.e., CUs and DUs managed by network operators) via the standard E2 interface [6]. It includes RAN- and UE-related telemetry that is collected by a MobiFlow Auditor embedded into the CUs and DUs, as they process and relay all the cellular communication traffic between the UE and the network.
MobiFlow will provide security audit services within a wide range of O-RAN-compliant operational network infrastructures, allowing them to detect L3 exploits in real-time. Therefore, we will actively work with the O-RAN working groups to propose integrating our MobiFlow security telemetry service into their reference service model implementations, and emphasize its security implication to the O-RAN community.
Defending O-RANs from Hostile RF Ecosystems
Another aspect of our activities will be to create reference OSS xApp security services that demonstrate the power of MobiFlow-based analytics and the open extensibility of the O-RAN RIC framework. Initially, we intend to introduce mobile infrastructure-resident layer-3 IDS services that can detect all the published active-insertion L3 exploits that have plagued 4G networks and persist within 5G. Many new security xApps will follow this model, including RAN-wide anomaly detection services and machine learning algorithms capable of automating malicious pattern classification.
Our initial effort is the development of 5G-Spector, the first comprehensive Layer-3 malicious RF detection system, implemented as an O-RAN xApp. Its objective is to enable network experts (e.g., operators and maintainers) to easily program detection logic integrated into a xApp that works as an intrusion detection system (IDS) to defend networks from adversarial RF devices, such as malicious SDRs. At a high level, 5G-Spector takes the fine-grained MobiFlow stream from the RIC to monitor the L3 activities at the data plane, and produces real-time alerts and notifications to the users.
Currently, we have instantiated a prototype of 5G-Spector, exploring two key aspects of algorithm design: (1) programmability that enables network operators to define production rule-based IDS logic using an efficient programming language, and (2) flexibility, as it is a lightweight “plug-n-play” xApp and can be easily integrated into the 5G O-RAN control plane without adding much performance overhead. 5G-Spector’s design is powered by the Production-Based Expert System Toolset (P-BEST) language [47], which has been widely used for decades in stateful intrusion detection [47, 46, 72, 49, 19]. The P-BEST language has also been proven to have a low learning threshold via a user study, where over 70% of the participating students were able to successfully write a P-BEST system to detect malicious FTP traffic within four hours [47]. It features a decoupled architecture that separates detection mechanisms from the system implementation and also provides an efficient production-based rule expression language that compiles into C applications. Forward-reasoning inference engines are ideal for conducting (stateful) runtime protocol analysis to identify illegal sequences, multi-state conditions, temporal threshold violations, or other malicious patterns, which are all optimal capabilities for efficiently detecting the layer-3 exploits that we have collected and analyzed to date. We intend to enhance and further evaluate 5G-Spector during future 5G Super Blueprint integration sprints.
A 5G Open-Source Ecosystem that Supports Security
We hope to work closely with the 5G OSS community toward a dramatic improvement in the security and resilience of O-RAN-compliant projects and component solutions. This includes working with the Nephio and Linux Foundation 5G teams, and other top-tier 5G projects, to deliver reference implementations of MobiFlow into O-RAN-compliant CU/DU projects. We will also champion the extension of Open-RAN base-station software with audit services to enable advanced xApp-based security analytics. Mobile operators cannot secure their networks if they cannot see the security-relevant operations taking place among UEs and base stations. MobiFlow represents a first reference security-focused O-RAN E2SM service model [1, 8], and could lead to an adoptable reference standard. In addition, 5G-KubeArmor is already an Apache 2 OSS project (with its core analysis engine governed under the CNCF). We also anticipate the release of 5G-Spector as one of multiple potential OSS 5G security projects. These tools represent a rich set of modular services that can address the critical need to secure the data and control planes within the emerging O-RAN framework, particularly as mission-critical communities attempt to employ O-RAN-compliant infrastructure in their environments.
References
[1] O-RAN Specification. https://www.o-ran.org/specifications.
[2] USRP Software Defined Radio (SDR). https://www.ettus.com/products/.
[3] ORAN-WG3.E2SM-NI-v01.00: O-RAN Near-Real-time RAN Intelligent Controller E2 Service Model (E2SM), RAN Function Network Interface (NI) 1.0, February 2020.
[4] O-RAN.WG3.E2SM-RC-v01.03: O-RAN E2 Service Model (E2SM), RAN Control 1.03, October 2022.
[5] Threat Matrix for Kubernetes. https://microsoft.github.io/Threat-Matrix-for-Kubernetes/, July 2022.
[6] O-RAN.WG3.E2AP-R003-v03.00: O-RAN E2 Application Protocol (E2AP) 3.0, March 2023.
[7] O-RAN.WG3.E2SM-KPM-R003-v03.00: O-RAN E2 Service Model (E2SM) KPM 3.0, March 2023.
[8] O-RAN.WG3.E2SM-R003-v03.00: O-RAN E2 Service Model (E2SM) 3.0, Martch 2023.
[9] OAI / OpenAirInterface 5G. https://gitlab.eurecom.fr/oai/openairinterface5g, April 2023.
[10] 3GPP. Non-Access-Stratum (NAS) protocol for Evolved Packet System (EPS). http://www.3gpp. org/DynaReport/24301.htm.
[11] 3GPP. Radio Resource Control (RRC). http://www.3gpp.org/DynaReport/38331.htm.
[12] 3GPP. Study on 5G security enhancements against False Base Stations (FBS). http://www.3gpp.org/ DynaReport/33809.htm.
[13] Sangwook Bae, Mincheol Son, Dongkwan Kim, CheolJun Park, Jiho Lee, Sooel Son, and Yongdae Kim. Watching the Watchers: Practical Video Identification Attack in LTE Networks. In 31st USENIX Security Symposium (USENIX Security 22), pages 1307–1324, 2022.
[14] Evangelos Bitsikas and Christina P ̈opper. Don’t Hand It Over: Vulnerabilities in the Handover Procedure of Cellular Telecommunications. In Annual Computer Security Applications Conference, pages 900–915, 2021.
[15] Evangelos Bitsikas and Christina P ̈opper. You Have Been Warned: Abusing 5G’s Warning and Emergency Systems. In Proceedings of the 38th Annual Computer Security Applications Conference, pages 561–575, 2022.
[16] Ravishankar Borgaonkar, Andrew Martin, Shinjo Park, Altaf Shaik, and Jean-Pierre Seifert. White-stingray: evaluating IMSI catchers detection applications. USENIX, 2017.
[17] Jay Chen. Graboid: First-Ever Cryptojacking Worm Found in Images on Docker Hub. https://unit42.paloaltonetworks.com/graboid-first-ever-cryptojacking-worm-found-in-images-on-docker-hub/, October 2019.
[18] Yi Chen, Yepeng Yao, XiaoFeng Wang, Dandan Xu, Chang Yue, Xiaozhong Liu, Kai Chen, Haixu Tang, and Baoxu Liu. Bookworm Game: Automatic Discovery of LTE Vulnerabilities Through Documentation Analysis. In 2021 IEEE Symposium on Security and Privacy (SP), pages 1197–1214. IEEE, 2021.
[19] S. Cheung, U. Lindqvist, and M.W. Fong. Modeling Multistep Cyber Attacks for Scenario Recognition. In Proceedings of the Third DARPA Information Survivability Conference and Exposition (DISCEX III), pages 284–292. DARPA, 2003.
[20] Stefano Chierici. Hands-On Muhstik Botnet: crypto-mining attacks targeting Kubernetes. https://sysdig.com/blog/muhstik-malware-botnet-analysis/, November 2021.
[21] Stefano Chierici. THREAT ALERT: Crypto miner attack – Sysrv-Hello Botnet targeting WordPress pods. https://sysdig.com/blog/crypto-sysrv-hello-wordpress/, August 2021.
[22] Merlin Chlosta, David Rupprecht, Christina P ̈opper, and Thorsten Holz. 5G SUCI-Catchers: Still catching them all? 2021.
[23] Lucian Constantin. Half of all Docker Hub images have at least one critical vulnerability. https://www.csoonline.com/article/3599454/half-of-all-docker-hub-images-have-at-least-one-critical-vulnerability.html, December 2020.
[24] Adrian Dabrowski, Nicola Pianta, Thomas Klepp, Martin Mulazzani, and Edgar Weippl. IMSI-catch me if you can: IMSI-catcher-catchers. In Proceedings of the 30th annual computer security applications Conference, pages 246–255, 2014.
[25] Chris Duckett. OMIGOD: Azure users running Linux VMs need to update now. https://www.zdnet.com/article/omigod-azure-users-running-linux-vms-need-to-update-now/, September 2021.
[26] Mitziu Echeverria, Zeeshan Ahmed, Bincheng Wang, M Fareed Arif, Syed Rafiul Hussain, and Omar Chowdhury. PHOENIX: Device-Centric Cellular Network Protocol Monitoring using Runtime Verification.
[27] Simon Erni, Martin Kotuliak, Patrick Leu, Marc R ̈oschlin, and Srdjan Capkun. AdaptOver: adaptive overshadowing attacks in cellular networks. In Proceedings of the 28th Annual International Conference on Mobile Computing And Networking, pages 743–755, 2022.
[28] David Fiser and Alfredo Oliveira. TeamTNT Upgrades Arsenal, Refines Focus on Kubernetes and GPU Environments. https://www.trendmicro.com/en_no/research/21/k/teamtnt-upgrades-arsenal-refines-focus-on-kubernetes-and-gpu-env.html, November 2021.
[29] David Fizer. TeamTNT Now Deploying DDoS-Capable IRC Bot TNTbotinger. https://www.trendmicro.com/en_us/research/20/l/teamtnt-now-deploying-ddos-capable-irc-bot-tntbotinger.html, December 2020.
[30] Ismael Gomez-Miguelez, Andres Garcia-Saavedra, Paul D Sutton, Pablo Serrano, Cristina Cano, and Doug J Leith. srsLTE: An open-source platform for LTE evolution and experimentation. In Proceedings of the Tenth ACM International Workshop on Wireless Network Testbeds, Experimental Evaluation, and Characterization, pages 25–32, 2016.
[31] Syed Hussain, Omar Chowdhury, Shagufta Mehnaz, and Elisa Bertino. LTEInspector: A systematic approach for adversarial testing of 4G LTE. In Network and Distributed Systems Security (NDSS) Symposium 2018, 2018.
[32] Syed Rafiul Hussain, Mitziu Echeverria, Omar Chowdhury, Ninghui Li, and Elisa Bertino. Privacy attacks to the 4G and 5G cellular paging protocols using side channel information. Network and Distributed Systems Security (NDSS) Symposium2019, 2019.
[33] Syed Rafiul Hussain, Mitziu Echeverria, Imtiaz Karim, Omar Chowdhury, and Elisa Bertino. 5GReasoner: A property-directed security and privacy analysis framework for 5G cellular network protocol. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, pages 669–684, 2019.
[34] Syed Rafiul Hussain, Mitziu Echeverria, Ankush Singla, Omar Chowdhury, and Elisa Bertino. Insecure connection bootstrapping in cellular networks: the root of all evil. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, pages 1–11, 2019.
[35] Syed Rafiul Hussain, Imtiaz Karim, Abdullah Al Ishtiaq, Omar Chowdhury, and Elisa Bertino. Non-compliance as Deviant Behavior: An Automated Black-box Noncompliance Checker for 4G LTE Cellular Devices. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, pages 1082–1099, 2021.
[36] McAfee Inc. MVISION Insights: Xanthe: A Docker-Aware Miner. https://kc.mcafee.com/corporate/index?page=content&id=KB94179, February 2021.
[37] IronNet. A sobering reminder for more vigilant supply chain security. https://securityboulevard.com/2020/12/a-sobering-reminder-for-more-vigilant-supply-chain-security/, December 2020.
[38] Roger Piqueras Jover. LTE security, protocol exploits and location tracking experimentation with low-cost software radio. arXiv preprint arXiv:1607.05171, 2016.
[39] Hongil Kim, Jiho Lee, Eunkyu Lee, and Yongdae Kim. Touching the untouchables: Dynamic security analysis of the LTE control plane. In 2019 IEEE Symposium on Security and Privacy (SP), pages 1153–1168. IEEE, 2019.
[40] Anton Kirillov. Cryptomining Attacks on Kubeflow: What You Need to Know. https://d2iq.com/blog/what-you-need-to-know-about/-cryptomining-attacks-on-kubeflow, June 2021.
[41] Martin Kotuliak, Simon Erni, Patrick Leu, Marc Roeschlin, and Srdjan ˇCapkun. LTrack: Stealthy Tracking of Mobile Phones in LTE. In 31st USENIX Security Symposium (USENIX Security 22), pages 1291–1306, 2022.
[42] Ravii Lakshmanan. SolarWinds Hackers Targeting Government and Business Entities World-wide. https://thehackernews.com/2021/12/solarwinds-hackers-targeting-government.html, December 2021.
[43] Ravie Laksmanan. Microsoft Warns of Cross-Account Takeover Bug in Azure Container Instances. https://thehackernews.com/2021/09/microsoft-warns-of-cross-account.html, September 2021.
[44] Gyuhong Lee, Jihoon Lee, Jinsung Lee, Youngbin Im, Max Hollingsworth, Eric Wustrow, Dirk Grunwald, and Sangtae Ha. This is your president speaking: Spoofing alerts in 4G LTE networks. In Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services, pages 404–416, 2019.
[45] Zhenhua Li, Weiwei Wang, Christo Wilson, Jian Chen, Chen Qian, Taeho Jung, Lan Zhang, Kebin Liu, Xiangyang Li, and Yunhao Liu. FBS-Radar: Uncovering Fake Base Stations at Scale in the Wild. In NDSS, 2017.
[46] U. Lindqvist and P. Porras. EXpert-BSM: A Host-Based Intrusion Detection Solution for Sun Solaris. In Proceedings of the 17th Annual Computer Security Applications Conference. IEEE Computer Society, 2001.
[47] Ulf Lindqvist and Phillip A Porras. Detecting computer and network misuse through the production-based expert system toolset (P-BEST). In Proceedings of the 1999 IEEE Symposium on Security and Privacy (Cat. No. 99CB36344), pages 146–161. IEEE, 1999.
[48] Norbert Ludant and Guevara Noubir. SigUnder: a stealthy 5G low power attack and defenses. In Proceedings of the 14th ACM Conference on Security and Privacy in Wireless and Mobile Networks, pages 250–260, 2021.
[49] Teresa Lunt, Ann Tamaru, Fred Gilham, Ramesh Jagannathan, Caveh Jalali, Peter Neumann, Harold Javitz, and Thomas Garvey. A Real-Time Intrusion-Detection Expert System. 01 1992.
[50] Malpedia. A list of TNTExploits and Analyses. https://malpedia.caad.fkie.fraunhofer.de/details/elf.teamtnt, April 2021.
[51] Prajwol Kumar Nakarmi, Mehmet Akif Ersoy, Elif Ustundag Soykan, and Karl Norrman. Murat: Multi-RAT False Base Station Detector. arXiv preprint arXiv:2102.08780, 2021.
[52] Peter Ney, Ian Smith, Gabriel Cadamuro, and Tadayoshi Kohno. SeaGlass: Enabling City-Wide IMSI-catcher Detection. Proc. Priv. Enhancing Technol., 2017(3):39, 2017.
[53] Shaun Nichols. Russia using Kubernetes cluster for brute-force attacks. https://www.techtarget.com/searchsecurity/news/252503482/Russia-using-Kubernetes-cluster-for-brute-force-attacks, July 2021.
[54] Nuand. bladeRF. https://www.nuand.com/bladerf-1.
[55] Nir Ohfeld and Sagi Tzadik. ChaosDB: How we hacked thousands of Azure customers’ databases.
[56] C Park, Sangwook Bae, B Oh, Jiho Lee, Eunkyu Lee, Insu Yun, and Yongdae Kim. DoLTEst: In-depth Downlink Negative Testing Framework for LTE Devices. In USENIX Security Symposium, 2022.
[57] Phillip Porras. Cloud Security Year-end Review. https://www.accuknox.com/blog/2021-cloud-security-year-end-review, January 2022.
[58] Dark Reading. Software-Container Supply Chain Sees Spike in Attacks. https://www.darkreading.com/cloud/software-container-supply-chain-sees-spike-in-attacks/d/d-id/1341353, June 2021.
[59] David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina P ̈opper. Breaking LTE on Layer Two. In 2019 IEEE Symposium on Security and Privacy (SP), pages 1121–1136. IEEE, 2019.
[60] David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina P ̈opper. Call Me Maybe: Eavesdropping Encrypted {LTE} Calls With ReVoLTE. In 29th USENIX Security Symposium (USENIX Security 20), pages 73–88, 2020.
[61] David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina P ̈opper. IMP4GT: IMPersonation Attacks in 4G NeTworks. In Proceedings of the 27th Annual Network and Distributed System Security Symposium (NDSS’20), 2020.
[62] Aviv Sausson. 20 Million Miners: Finding Malicious Cryptojacking Images in Docker Hub. https: //unit42.paloaltonetworks.com/malicious-cryptojacking-images/, March 2021.
[63] Tara Seals. Kubernetes Cloud Clusters Face Cyberattacks via Argo Workflows. https://threatpost.com/kubernetes-cyberattacks-argo-workflows/167997/, July 2021.
[64] Altaf Shaik, Ravishankar Borgaonkar, N Asokan, Valtteri Niemi, and Jean-Pierre Seifert. Practical Attacks Against Privacy and Availability in 4G/LTE Mobile Communication Systems. 2016.
[65] Ankush Singla, Rouzbeh Behnia, Syed Rafiul Hussain, Attila Yavuz, and Elisa Bertino. Look Before You Leap: Secure Connection Bootstrapping for 5G Networks to Defend Against Fake Base-Stations. In Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security, pages 501–515, 2021.
[66] LF Networking 5G Team. The 5G Super Blueprint Project Page. https://lfnetworking.org/5g-super-blueprint/, April 2023.
[67] Bill Toulas. TeamTNT hackers target your poorly configured Docker servers. https://www.bleepingcomputer.com/news/security/teamtnt-hackers-target-your-poorly-configured-docker-servers/, November 2021.
[68] Liam Tung. US warns Log4j flaw puts hundreds of millions of devices at risk. https://www.zdnet.com/article/log4j-flaw-puts-hundreds-of-millions-of-devices-at-risk-says-us-cybersecurity-agency/ December 2021.
[69] Lisa Vaas. Windows Container Malware Targets Kubernetes Clusters. https://threatpost.com/windows-containers-malware-targets-kubernetes/166692/, June 2021.
[70] Fabricio Voznika and Mauricio Poppe. A Storage Vulnerability Deep Dive. https://websecurity.agency/a-storage-vulnerability-deep-dive/, December 2021.
[71] Yuchen Wang, Zhenfeng Zhang, and Yongquan Xie. Privacy-Preserving and Standard-Compatible AKA Protocol for 5G. In 30th USENIX Security Symposium (USENIX Security 21), 2021.
[71] Haohuang Wen, Phillip Porras, Vinod Yegneswaran, and Zhiqiang Lin. A Fine-grained Telemetry Stream for Security Services in 5G Open Radio Access Networks. In Proceedings of the 1st International Workshop on Emerging Topics in Wireless, pages 18–23, 2022.
[72] R. A. Whitehurst, M. M. Sebring, E. Shellhouse, and M. E Hanna. Expert systems in intrusion detection: a case study. In Proceeding of the 11th National Computer Security Conference, 1988.
[73] Hojoon Yang, Sangwook Bae, Mincheol Son, Hongil Kim, Song Min Kim, and Yongdae Kim. Hiding in Plain Signal: Physical Signal Overshadowing Attack on LTE. In 28th USENIX Security Symposium (USENIX Security 19), pages 55–72, 2019.